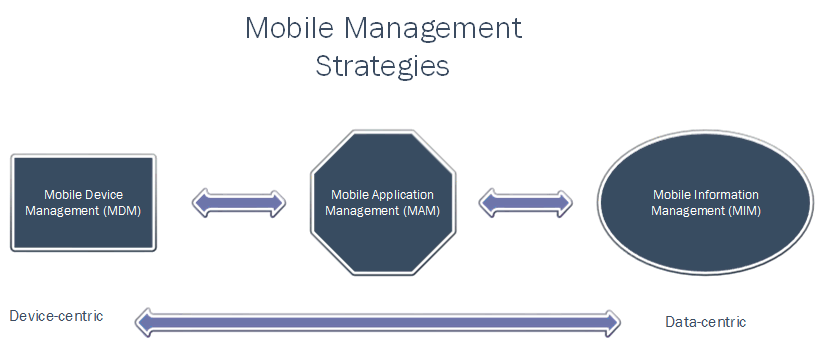
Like many of my colleagues in higher education, I’m struggling to get my head around this mobile thingy. In the changing environment of mobile technology with an ever-growing number of devices and operating systems, the conventional strategy of tightly controlling devices becomes more of a losing proposition. Many of my colleagues continue to think about mobile devices using the traditional paradigm of the laptop computer, running a business OS, that can be tightly controlled. This strategy of mobile device management (MDM) is the oldest and most mature of the three mobile management strategies, but it is dependent upon the assumption that the device ecosystem is a known universe – an increasingly tenuous assumption. For MDM to work, device type and configuration must be simplified in order for IT’s limited resources to effectively manage them. This strategy becomes problematic when a significant number of users (faculty, staff and students) are bringing their own devices to town (i.e. BYOD, BYOP, BYOT, BYOPC, etc.) and expect to access data, which brings us to the second strategy.
Mobile Application Management (MAM) does not seek to control the device, but rather contain protected data within a “sandbox”, and thus limit the user’s interaction with the data. Examples of this would be virtual application and desktop environments. This strategy has the advantage of device agnosticism, but also must stay one step ahead of those who would attempt to break the sides of the sandbox and access the data in an unauthorized manner. The last strategy (and least developed) is mobile information management (MIM). In this universe, the data never actually reside on the device, at least in a format that is generally accessible. Digital Rights Management schema are one method of MIM. Providing a container for data that is subsequently displayed as a raster or some other digitally inaccessible format is another strategy. An immutable, tamper-resistant client with no local storage is the gold standard of this model.
All of these issues are components of the end-node problem, which is the real crux of the mobile quandary. In a nutshell, in most conventional networks, there are an unknown number and type of clients connecting at unknown times and with varying states of security. Authentication schema such as two-factor authentication can go a long way to creating a more secure data ecosystem. TAMU is in the process of moving to two-fact authentication, but it could be a year or two before we’re there.
Not to be confused with the technical management strategy, mobile devices also introduce administrative questions that have nothing to do with security or technical control. In the new mobile device ecosystem, users are using their mobile devices for a variety of tasks, not all of them business related and most of them insecure. Netflix, Hulu, Drop Box, literally tens of thousands of mobile applications designed for end-user convenience and entertainment, not end-user security, are in the market. Many of these mobile devices, some purchased with university funds, are being used for non-business reasons, although many would suggest that this type of usage, hopefully after-hours would fall under incidental use. One strategy is to use MDM to prevent installation and therefore usage of these “unauthorized” applications. But is a technical lock the best solution to solve an arguably ethical problem? Is it IT’s role to define and administer policy with restrictive configurations? The answer is still out.