Protecting Yourself

From Cybercrimes & Identity Theft
In 2020 it was estimated that 591,857 Americans were victims of identity-based crimes including fraud and identity theft. Of them 241,342 Americans fell victim to phishing, vishing and smishing attacks.
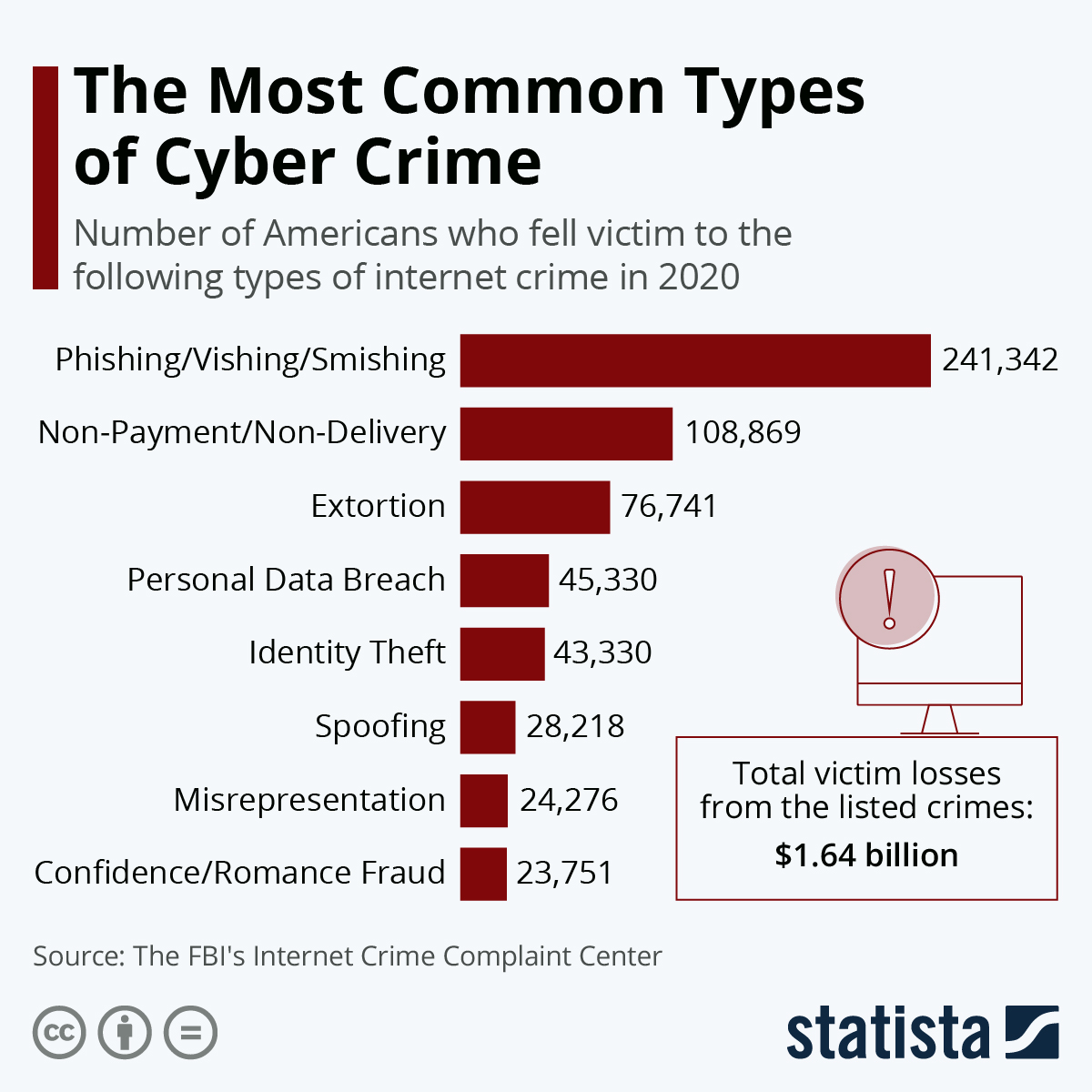 Source: https://www.statista.com/chart/24593/most-common-types-of-cyber-crime/
Source: https://www.statista.com/chart/24593/most-common-types-of-cyber-crime/
October is Cybersecurity Awareness Month and at Technology Services – Student Affairs we thought we’d kick things off a couple of days early and help you to understand some ways that identity theft can occur. We wanted to give you some tips on how to avoid identity theft and, may be, even reduce the number of telemarketers calling you!
Help us keep Texas A&M safe, while you keeping yourself safe.
Many people think that cyber-crimes are performed by some guy, in a dark room with a huge computer, typing code into a keyboard, but most of these crimes are done through something called Social Engineering.

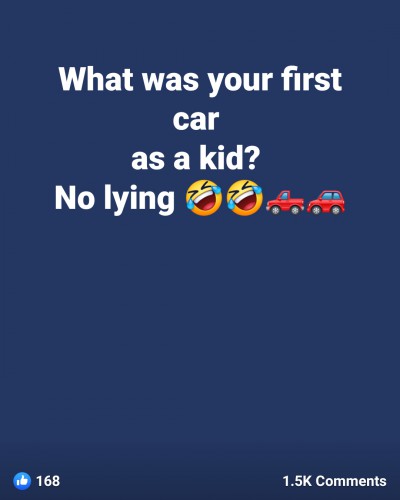
For example, have you ever seen something like this on Facebook? This was something shared by an automotive dealership, and it seems harmless, right? The thing is, many people use the question “what was your first car” as a security question for recovering passwords. The comments revealed a number of people’s first and last names as well as the year, make, and model of their first car. Now the internet pretty much has the answer to that security question. No actual “hacking” was required. Just a simple Facebook search.

Another common method to obtain people’s personal data is through Phishing emails. These emails are made to look like official emails from reputable companies. A common theme is emails from a bank or some financial institution. They may contain messages offering you a new deal or telling you something is wrong with your account. They might even be emails that look like they are from your bank telling you there has been some suspicious activity on your account, and you need to log in immediately.
When you click the login link in the email it takes you to a site that looks exactly like the homepage or login for your bank account. Only that they are not the actual sites. They are fake sites created to lure you in and make you reveal sensitive information about yourself and/or your finances. Now these scamsters have what they need to steal your money. However you can protect yourself. Pay attention to the web address. In doing so you may notice some odd things such as three “l”s in Wells Fargo or dot con instead of a dot com. This should warn you not to proceed. The best advice is never open a “login” link from inside an email. Instead, type the correct link into your browser yourself.
In the table below are some of the common examples of such suspicious URLs. See if you can spot the difference between the legitimate web address and the fraudulent examples below.
| Addresses! | Real or Fake? |
|---|---|
| https://www.usbank.con | https://www.usbank.com |
| https://www.wellsfargo.com | https://www.welllsfargo.com |
| https://www.tamù.edu | https://www.tamu.edu |
| https://www.netflix.com | https://www.netfliх.com |
So how many did you get?
Actually, in all four cases one address was real while the other was fake. It is hard to tell, especially if you are in a hurry or worried about suspicious activity in your bank account. Sometimes it is just impossible to tell the difference. In the case of Netflix, the x in “Netflix” is using a foreign character instead of a Latin character. In this case it is “Kha” or “Ha” a letter of the Cyrillic script. It looks the same as the Latin letter X, in both uppercase and lowercase. The fake URL would (Ha Ha) take you to a fake site.

Another way emails can harm you is by infecting your computer with malware. Suspicious emails may have malicious programs hidden inside them that are downloaded onto your computer as soon as you open the email. You don’t have to download anything, just open the email, and it’s on your computer. These programs can do several things such as sending website history to someone, logging everything you type on your keyboard, use your address book to send similar malicious emails to others, or just wipe out your hard drive .

Email isn’t the only way cybercriminals try to scam you. Telephone calls is a very popular method too. Have you received the “We’ve been trying to reach you about your car’s extended warranty” call yet? Or maybe “This is the IRS, and you owe thousands of dollars in back taxes, pay now or you’ll go to jail.” While some calls may just be annoying ,others are more malicious and could cause you significant financial loss. The best way to protect yourself is to educate yourself.
We recommend stopping by the Division of IT’s Cyber Security Page. It is an amazing resource for learning how scams work, how to recognize scams, and how to avoid them.
There you can read about how to protect your identity and your devices, learn about things to look out for when it comes to scams, and even play some games to help you learn to recognize scams before you become a victim.


