Understand How to Report Phishing Attempts

In February 2020, Indian TV journalist Nidhi Razdan announced that she was leaving her 21-year-old job with New Delhi based English TV news channel NDTV 24*7 to be an associate professor at Harvard University, or so she thought. Razdan was approached by someone who claimed to be from Harvard, submitted her resume, and even interviewed online for 90 minutes. Next, she received the “offer letter.” She quit her job and began to plan her move to Harvard. However, she eventually realized that she was a victim of an elaborate phishing scam and there were no records of her appointment at Harvard. [1]
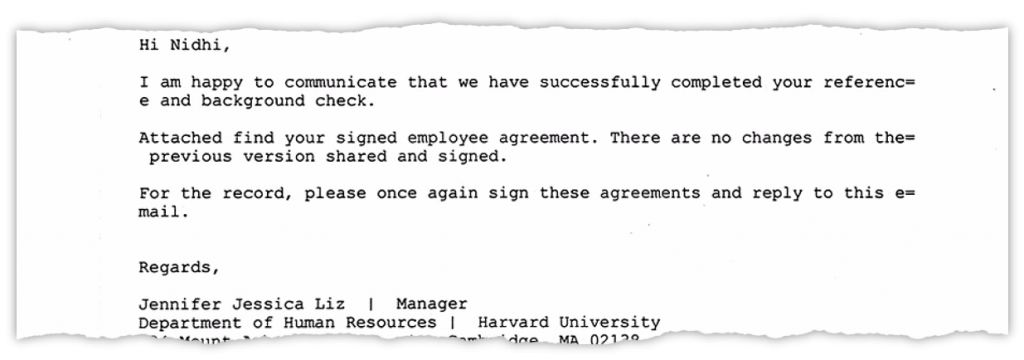

This was an incident of a phishing attack with the possible intention of stealing personal data and money. Since the pandemic began, the world has turned more virtual in its communication and interaction. We do not, now, consider a completely virtual interaction to be unusual. This has opened the doors to more numerous and increasingly sophisticated phishing attacks.
Everyone who has an email has, at some point, received an email that is designed to take advantage of you. Sometimes we don’t hear about the phishing scam itself, which is an attempt to get you to provide personal information, financial information, or want you to click on a link or attachment that will allow for viruses or malware to infect your computer. What we do hear about is a stolen identity, hacked bank account, or one of many other adverse outcomes from phishing email scams. Over the last couple of years, attempts to get you to take action on a phishing email have gotten very sophisticated and can even appear to be from trusted sources, like your bank, your job, a reputed organization or even friends and family.
What is phishing?
Phishing emails are scams that seem to come from a trusted source or a trusted email sender but trick you into giving up private information or taking risky actions.
Phishing explained
Phishing scams are typically fraudulent email messages appearing to come from legitimate enterprises (for example, your university, your internet service provider, your bank). These messages usually direct you to a spoofed website or otherwise get you to divulge private information (for example, passphrase, credit card, or other account updates). The perpetrators then use this private information to commit identity theft.
One type of phishing attempt is an email message stating that you are receiving it due to fraudulent activity on your account, and asking you to “click here” to verify your information.
Phishing scams while appearing legitimate and sophisticated are really crude social engineering tools designed to induce panic in the reader. These scams attempt to trick recipients into responding or clicking immediately, by claiming they will lose something (for example, email, bank account). Such a claim is always indicative of a phishing scam, and responsible companies and organizations will never take these types of actions via email.
One of the common techniques used in phishing emails is “email spoofing.” This is where the sender will forge their address to make it appear as though it came from a trusted source. When in doubt, contact the sender through other means before clicking anything in the email.
In the table below are some of the common examples of such suspicious URLs. See if you can spot the difference between the legitimate web address and the fraudulent examples below.
Actually, in all four cases, one address was real while the other was fake. Sometimes it is just impossible to tell the difference. In the case of Netflix, the x in “Netflix” is using a foreign character instead of a Latin character. In this case, it is “Kha” or “Ha” a letter of the Cyrillic script. It looks the same as the Latin letter X, in both uppercase and lowercase. The fake URL would take you to a fake site.
Can I prevent it?
YES!
- Think before you click:
Do you recognize the sender, if not, or if you are unsure, verify the sender is who you think it is?
How: Double-click or tap the sender’s name at the top of the email to view the real email address. (In Gmail, hover without clicking.) - Rethink clicking the link if you can’t verify the sender. When in doubt do not click at all.
How: If the email refers to a known website, type that website address into a new browser window instead and check for information there. - Suspect it’s a phish but not sure, ask for help.
How: Contact Technology Services – Student Affairs for help. - Pay attention to the web addresses.
TAMU offers resources to help you find some guidelines to protect yourself from these attempts.
- TAMU Resource for Phishing Scams
- TAMU Resource for protecting your identity
- TAMU Resource for Safe Computing
Even with TAMU’s sophisticated security measures, YOU are still the best defense against scam emails.
Steps TAMU has taken recently to make its email safe:
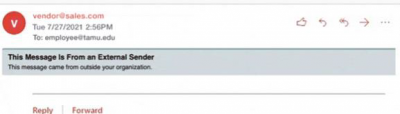
Emails sent to your TAMU email account now have warning tags when they come from external senders.
A gray tag identifies an email sent from an external sender
A yellow tag identifies an email sent from a suspicious and potentially malicious source

Extra Protection for URLs sent through Internal Exchange and Teams Messages:
Beginning February 22, 2022, internal messages sent between Texas A&M Exchange and Teams users will now be scanned with Microsoft 365 Defender. The URLs will be checked against Microsoft threat intelligence. If the link leads to an attachment, it will also be scanned for malware. if the link is malicious a warning screen will appear indicating a site may be dangerous. There is an option to continue to the website, but it is not recommended.
Reference:
[1] Jeffrey Gettleman, “The Harvard Job Offer No One at Harvard Ever Heard Of,” The New York Times, December 16, 2021. https://www.nytimes.com/2021/12/16/technology/harvard-job-scam-india.html
